If you’re planning to build a Health Information Exchange (HIE)—whether as a government agency, public-sector contractor, TPA, provider, or technology vendor—one challenge is impossible to ignore: establishing health information exchange security, and engaging experienced HIE software development services to get it right.
Modern HIEs are designed to connect hospitals, labs, insurers, and public health systems. They consolidate massive volumes of patient data from multiple organizations into a single, multi-tenant healthcare platform. This architecture enhances interoperability while also raising the bar for compliance and data security in HIE systems.
Healthcare data breaches increased by 156% in 2023, with 133 million records compromised, or 374,000 each day on average. Healthcare is now the most expensive industry for cybersecurity breaches, with a single breach costing an average of $9.77 million.

These numbers are a clear warning for those launching HIEs today: tenant isolation, access control, and auditability are no longer “advanced features”; they are now baseline requirements.
In this article, we provide a comprehensive guide to healthcare system security best practices in multi-tenant HIE setups, offering actionable insights for healthcare IT leaders, security specialists, and system architects responsible for protecting sensitive patient information across organizational boundaries.
Highlights:
- Healthcare data breaches jumped 156% in 2023, leaving 133 million records open to attack
- A healthcare data breach now costs $9.77 million on average
- Healthcare now leads as the most expensive sector for cybersecurity incidents.
Why HIE Security Is a Complex Topic
Scaling a HIE securely across multiple tenants brings a unique set of challenges. Each organization—hospitals, clinics, insurers, pharmacies—operates under different permissions, compliance rules, and data usage needs, making health IT security architecture more complex than in single-organization systems.
In multi-tenant environments, shared secure health IT infrastructure increases the risk of:
- Misconfigured access policies, allowing unauthorized data exposure.
- Cross-tenant data leaks, where sensitive information moves between organizations improperly.
- Limited audit visibility, making it harder to monitor activities or prove compliance.
- Unmanaged APIs, which attackers can exploit to access critical systems directly.
These risks are real and must be managed carefully. In Edenlab’s National E-Health System implementation, which handles 36.5 million patient records across 8,275 medical facilities and 15,000 pharmacies, addressing these risks was a top priority. The project placed a strong focus on tenant isolation, strict role-based access control, and securing API layers, demonstrating how scalable, compliant HIE infrastructure can be built, even at a national healthcare systems level.
Security Considerations Across Different HIE Models
The architecture and purpose of an HIE directly shape its healthcare data exchange security requirements. Whether national or local, government-led or business-driven, each model presents unique risks and demands tailored protections from day one.
- Government-mandated HIEs may function on a nationwide or regional scale, combining patient data from hundreds of institutions. These systems must enforce strong tenant isolation, facilitate cross-jurisdictional compliance (e.g., GDPR or HIPAA), and provide real-time auditability and visibility.
- Private health exchanges, such as those built for TPAs, payers, or enterprise software vendors, face different challenges. In addition to high throughput and real-time data synchronization, they often require fine-grained access control for diverse user groups. In one recent project, a Hong Kong-based TPA needed to simplify provider directory access and streamline claims workflows, which was solved by integrating a FHIR Facade and a secure auto-adjudication engine. Learn more about the project.
- Local HIEs, serving individual hospital networks, ACOs, or IDNs, may seem less complex, but security remains just as critical. These systems must align closely with internal policies, provide role-based access down to the departmental level, and ensure seamless integration with EMRs and clinical applications without introducing new vulnerabilities.
Why FHIR Matters for Scalable HIEs
When building HIEs that involve diverse participants, potentially extending beyond your immediate network, adopting a FHIR-based data model emerges as the superior choice. At Edenlab, we leverage our expertise in the HL7 FHIR standard to revolutionize healthcare interoperability, offering unparalleled advantages for large-scale health information exchange:
- Standardization and interoperability. FHIR provides a common language for healthcare data. It ensures information flows smoothly between providers, platforms, and care settings.
- Flexibility and scalability. As your needs grow, FHIR grows with you. Its modular structure, combined with our microservices approach, means your HIE can expand to handle millions of patient records without slowing down.
- Real-time capabilities. Healthcare decisions can’t wait. Our event-driven system leverages FHIR to deliver up-to-date information when and where it’s needed, keeping your network responsive and efficient.
- Built-in security. While the FHIR specification does not define security protocols, we implement industry-standard security frameworks like OAuth 2.0 and OpenID Connect through implementation guides such as SMART on FHIR. These ensure secure, authorized cross-system patient data-sharing.
- Regulatory compliance. Our solutions, based on FHIR security best practices, are designed to meet various regulatory standards, such as HIPAA, ONC certification, GDPR, HTI-1, the EU AI Act, EHDS, and Gematik ISiK (Germany). We also enable adherence to standards like the International Patient Summary (IPS), which facilitates cross-border data exchange but is not a regulatory requirement.
Do you want to know more about what is FHIR? Read our recent article.
Core Security Requirements in Data Exchange
Building a multi-tenant secure health data exchange requires technical measures tailored for highly sensitive healthcare data and shared infrastructures. Below are the essential architectural elements that system architects should prioritize.
Encryption in Transit
Data encryption is essential to protect against interception and breaches. Industry standards recommend TLS 1.2+ for data in transit and AES-256 for storage. In healthcare information exchange, multiple levels of encryption are applied, including encrypted transport, database-level encryption, secure storage volumes, and protected application fields, to reduce the attack surface across the secure information exchange architecture.
Learn more about Edenlab’s secure-by-design development in our FHIR Software Development Services offering.
Access Controls (RBAC, ABAC, and Zero Trust)
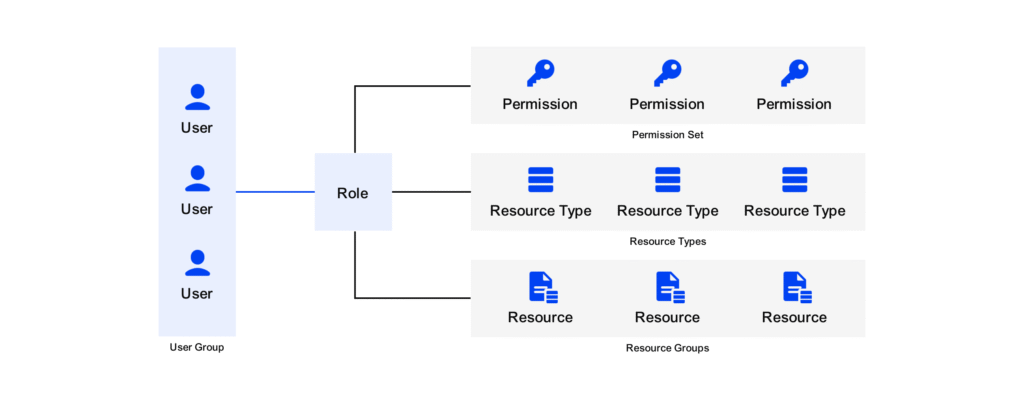
Securing multi-tenant HIEs begins with proper FHIR resource access control. Healthcare systems require a layered, adaptable strategy to ensure security and compliance as sensitive data flows between various organizations and user types. That’s where Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Zero Trust come in.
RBAC assures that users access just the information required for their role by assigning rights based on user functions, such as provider, payer, or administrator.
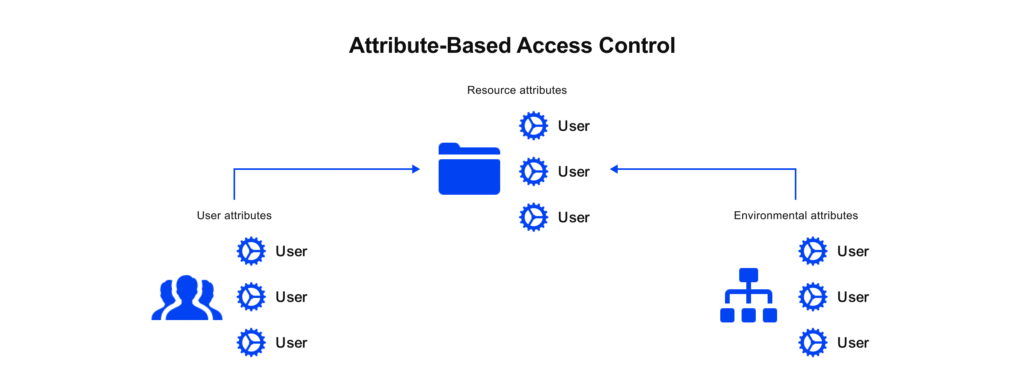
ABAC adds nuance by considering attributes such as a user’s location, device, or even the time of day. For example, access to a patient’s records might be limited to a clinician’s shift hours or granted only if explicit consent is recorded. ABAC provides healthcare systems with the flexibility to adapt to complex workflows without requiring frequent updates to access rules as processes change.
In the National Clinical Data Repository (NCDR) project, Edenlab developed an ABAC module that analyzes specific attributes to grant or deny access to health records, ensuring doctors can only view records from their institution while requiring patient approval for access. Learn more about the project.
The Zero Trust model goes further by requiring authentication and authorization at every access attempt, regardless of the network location or previous authentication. In healthcare, blending RBAC with Zero Trust principles provides usability for clinical workflows and enhanced defense against internal threats.
Identity and Token Lifecycle Management
Managing identity securely requires robust token strategies, such as OAuth 2.0 and OpenID Connect, to enable secure Single Sign-On (SSO). Token expiration should be clearly defined and supported by refresh policies to reduce vulnerability windows. At the same time, API keys must be validated, rotated, and tightly scoped as part of robust multi-tenant data governance practices. This approach minimizes risks such as token hijacking and replay attacks across multi-tenant environments.
Secure Storage by Tenant
Each tenant’s data must be logically separated to prevent accidental or malicious cross-access. Methods include using database schemas, row-level security, or even fully isolated databases per tenant. Separate encryption keys are managed per tenant, ensuring that even if one tenant’s key is compromised, others remain protected. An exemplary secure information exchange architecture is crucial for maintaining the scalability of HIE systems.
This approach was critical in our National E-Health System project, which securely manages tens of millions of patient records across thousands of organizations.
Consent Management
Managing patient consent is a cornerstone of secure and compliant health information exchange. Consent management systems track and enforce patients’ permissions regarding who can access their data, under what conditions, and for which purposes. This ensures that data sharing aligns with privacy laws and patient preferences.
Isolation, Compliance, and Resilience by Design
In shared HIEs, securing patient data in healthcare information exchange hinges on strict boundaries. To build a safe, compliant, and reliable multi-tenant architecture, you need to balance between access control, data residency, and disaster recovery.
Structuring Tenant-Specific Boundaries
In a multi-tenant HIE, it’s essential to isolate each tenant’s data to prevent unauthorized access or accidental data exposure. Key mechanisms include:
- ABAC. To securely separate data and actions across tenants, the ABAC approach is essential. ABAC evaluates user attributes, tenant context, and other factors, enabling fine-grained, context-aware access decisions. This method is crucial for implementing scoped APIs that protect sensitive data within shared environments.
- Scoped APIs. Design APIs to return only data relevant to the authenticated user’s tenant, thereby effectively preventing unauthorized data access across tenants.
- Network segmentation. Create logical or physical separation between tenant environments to limit potential breaches and reduce lateral movement within the system.
Meeting Per-Country Data Residency Requirements
Different countries have varying regulations regarding data residency—the requirement to store and process data within specific geographic boundaries. To comply with global standards like GDPR and national Ministry of Health (MOH) rules, HIE systems must be designed to support:
- Regional data centers. Store data within specific geographic regions to comply with local laws and regulations.
- Consent management. Ensure patients’ data is shared and stored based on explicit consent, as required by regulations such as GDPR healthcare compliance.
- Dynamic data classification. Automatically apply jurisdiction-specific policies to data based on the patient’s location.
Backup, Recovery, Versioning, and Long-Term Auditability
To maintain a resilient and compliant HIE, it’s vital to implement strategies for data protection and recovery:
- Backup and disaster recovery. Regular, encrypted backups of tenant-specific data are essential. Frequent testing guarantees that data can be recovered rapidly during a failure or assault. Establish Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) to ensure that essential systems are recovered within acceptable time frames following disruptions.
- Versioning systems. Implement versioning for patient data to ensure that any changes are tracked and previous states can be restored when needed. This helps prevent inadvertent or intentional data loss or manipulation without relying solely on backups.
- Auditability. Maintain thorough and secure audit records for extended periods of time, in accordance with HIPAA regulations, and ensure that data access and modifications can be traced back to their source.
Edenlab’s Backend Security Architecture
Edenlab’s backend security architecture is built around the Kodjin FHIR Data Platform, designed particularly for secure, multi-tenant HIEs, backed by our full cycle healthcare data platform development services. Rather than just a FHIR server, Kodjin serves as a complete technical foundation that ensures strict data isolation through separate schemas and OAuth 2.0 claims, while validating all incoming FHIR resources for structural and terminological accuracy to maintain high data quality.
The FHIR Access Control module is a key platform feature that provides granular, flexible access management compliant with SMART on FHIR and OAuth 2.0 standards, enabling precise control over who can access specific data. Kodjin’s scalable, event-driven architecture supports millions of records and thousands of concurrent users, with a robust audit trail and provenance tracking to ensure complete data access traceability and compliance with regulations.
In 2024, Cloud Torque and Edenlab joined forces, merging cloud expertise with healthcare innovation to transform FHIR services across Oceania. This powerful alliance leverages the Kodjin platform to deliver advanced interoperability solutions, setting a new standard in secure patient data exchange.
A practical demonstration of Kodjin’s capabilities is the Turbota Health Wallet, where Edenlab aggregated sensitive medical data from diverse sources while enforcing strict access controls, enabling millions of users to manage their health information securely. Overall, Edenlab’s Kodjin platform provides a secure, scalable, and compliant foundation for organizations building HIEs from scratch, supporting end-to-end development and co-development partnerships.
Conclusion
Security and compliance are now essential, not optional, for HIE data in healthcare companies due to the rise in security breaches and increasing regulatory requirements. Although multi-tenant HIEs are vital in facilitating interoperability, they also pose serious dangers in terms of system complexity and data vulnerability. A single hack has the potential to erode public confidence, compromise millions of documents, and have severe negative consequences for one’s finances and reputation.
If you’re planning to build a new HIE—whether at a national, regional, or enterprise level—success starts with security by design. By partnering with experienced teams and leveraging proven platforms like Kodjin, you can ensure your exchange is secure, compliant, and built to evolve with the healthcare landscape.
We dive deep where others skim
Our healthcare software development firm brings the expertise and precision needed to tackle the industry complexities. With a specialized focus on healthcare processes, regulations, and technology, we deliver solutions that address the toughest challenges.
FAQ
What are Health Information Exchange examples?
HIE covers multiple contexts, including clinics transmitting files to healthcare IT consultants, emergency departments retrieving patient records from other institutions, or individuals providing their medical information to new healthcare teams. Major platforms, such as Health Gorilla, CommonWell, and Carequality, enable these cross-system data transfers.
What does tenant isolation mean in healthcare?
Tenant isolation keeps each organization’s data separate and secure on shared platforms. Employees access only their own records, enabling HIPAA-compliant data exchange. This protects patient confidentiality and meets strict regulatory requirements, including HIPAA.
How does Edenlab support FHIR security modules?
Edenlab ensures FHIR security compliance through comprehensive FHIR authentication controls, permission systems, audit tracking, and data origin verification. These capabilities enable the secure exchange of data while maintaining regulatory compliance.
What’s the difference between user-level vs. tenant-level access control?
User-level access control sets what individuals can see or do based on their roles within an organization. Tenant-level access control, however, ensures that data remains separate between organizations. This is crucial in multi-tenant environments, such as shared cloud-based HIE platforms.
How do I validate if my existing HIE setup is secure enough?
Begin with a complete risk assessment to build a secure base for your HIPAA-compliant data exchange. Make sure you follow the relevant rules, check encryption methods, confirm access controls, and perform regular security checks to spot and fix possible weak points.
Stay in touch
Subscribe to get insights from FHIR experts, new case studies, articles and announcements
Great!
Our team we’ll be glad to share our expertise with you via email









